What is a Phishing Attack?
Phishing is a social engineering attack designed to steal user data such as login credentials, credit card numbers, and other personal information. The scam, which can come through as an email, text message, or instant message, masquerades as a trusted entity. It hopes you’ll bite and willingly hand over your information by clicking on a malicious link. The majority of these scams (51 percent) lead to a malware attack, according to Small Business Trends. With a malware attack, a hidden file gets installed on your computer. The file performs tasks such as making unauthorized purchases, stealing of funds, or initiating identify theft. Some malware attacks also hold your device hostage. In these cases, you’ll need to pay a bounty before regaining access to your computer.
How to Spot Scams?
When it comes to phishing scams, the first thing you need to embrace and remember is the idiom, if something seems too good to be true, it probably is. In more explicit terms, if you receive a text or email promising you quick cash or some prize, it’s almost certainly a scam. Unfortunately, these scams tend to get more cleaver with each passing year. Phishing scams can include, but aren’t limited to these examples:
Messages promising government refundsFreebies available with one clickNotices alerting you of a suspicious activity or log-in attemptsFake invoices that demand paymentNotice that your recent payment wasn’t accepted
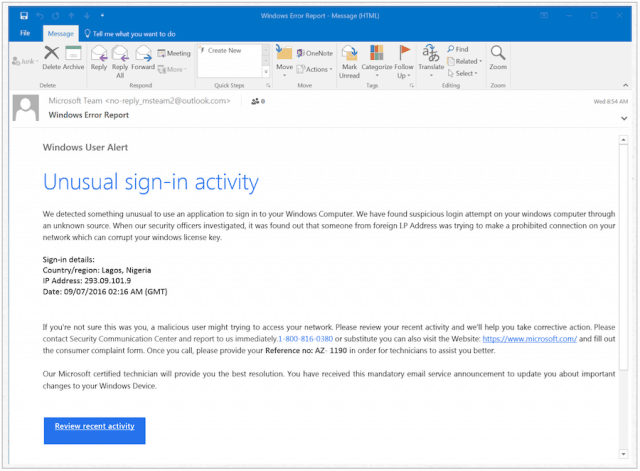
Examples
Phishing.org has published screenshots of real-life examples of scams. These include a fake Paypal security notice, a fake Microsoft notice, an attack on LinkedIn, among many others.
Here is an example of a Microsoft phishing message:
How to Protect Yourself from Phishing
To avoid becoming a victim of a phishing scheme, follow these essential steps:
Software Updates
The first thing you can do to protect yourself from phishing scams is to install security software on your device. And yes, this includes Macs, not just Windows. You should also make sure your computer’s operating system is always up-to-date. Make sure automatic updates are turned on to make this happen. Increasingly, mobile devices are no longer immune to phishing attacks. Therefore, also turn on automatic updates on your iOS and Android-based devices. Companies like Apple and Google do a great job of identifying and thwarting attacks. However, it’s up to you to make sure updates are installed on your devices promptly. You should also consider installing Google’s free phishing tool, which alerts you if you enter your Google account password somewhere other than accounts.google.com.
Use Multi-Factor Authentication
Increasingly, companies are offering or requiring multi-factor authentication to protect your account information. With this type of authentication enabled, you need to enter two or more credentials to log in to your account. For example, with multi-factor authentication — also called Two Factor Authentication or Two-Step Verification, you might be required to add a passcode that you receive through an email, text message, or authentication app. A scan of your fingerprint, retina, or face could also be required, depending on the organization. Always use multi-factor authentication when offered; if you aren’t given a choice, question whether you should be doing business with that organization.
Yes, Use a Strong Password
You also need to create strong passwords and keep them safe. To better protect your passwords, consider:
Using 10-12 characters for your passwordDon’t use names, dates, or common words in your passwords. Instead, use a mix of numbers, characters, and symbols. Also, use a combination of upper- and lowercase charactersDon’t use the same password with various accountsConsider purchasing a password-generator app/service like 1Password or Dashlane.Don’t share passwords over the phone, or through email/text.If you must write down a password, make sure it’s locked and out of plain sight.
Only Make Purchases on Secure Sites
In 2019, no one should be purchasing items on an unsecured website. Unfortunately, it still happens. To make sure the site you’re visiting is secure, look for the https at the beginning of the web address.
Back-Up Your Data
Finally, make sure to regularly back up your data using an external hard drive or cloud storage. That way, if there are problems, you can get back online as quickly as possible.
It’s Probably a Scam, Now What?
If you suspect an email or message received is a scam, you should first ask yourself whether you recognize the account or company that has made contact. If the answer is no, report the message, then delete it from your device. If the answer is yes, you should contact the company directly using a phone number or website you know as legitimate. Are you worried you already responded to a phishing scheme? In this case, visit IdentifyTheft.gov and follow the steps to take based on the information you fear that you lost.
You should also take things a step further and report the phishing to the authorities. A good starting point for this is to contact the FTC. At the FTC website, you’ll be asked to choose a complaint category and subcategory. If you can’t find a match, select the “Something Else” option. From there, you’ll need to answer a few questions related to your complaint and tell them what happened in your words. Phishing scams, unfortunately, aren’t going away, but there are things you can do to protect yourself. Following these steps will go a long way to adding more levels of security to your device. Peace of mind will follow!
![]()